Display Options
1552173897
Q!!mG7VJxZNCI 03/09/2019 18:24:57 ID: a61e11
8chan/qresearch: 5595092Q Clock [ Min: 37 | :25/:55 Mir: 13 | 180 Mir: 7 | :35/:05 Mir: 33 ]
Delta to Reply: 0 D_00:30:30 (seconds total: 1830) (12) (3)
Epoch: 1552172067 (36) (9)
Anonymous 03/09/2019 17:54:27 ID:b9886a 8chan/qresearch: 5594428
100%
Image Name: ClipboardImage.png
Filename: f4d2c71197a14b514b4effdebbdaaddd2bf1b0e8f879e681565189060590f21d.png
EXIF DATA
name : f4d2c71197a14b514b4effdebbdaaddd2bf1b0e8f879e681565189060590f21d.png
format : PNG
formatDescription : Portable Network Graphics
mimeType : image/png
class : DirectClass
geometry.width : 1522
geometry.height : 2042
geometry.x : 0
geometry.y : 0
units : Undefined
type : TrueColorAlpha
endianess : Undefined
colorspace : sRGB
depth : 8
baseDepth : 8
channelDepth.alpha : 1
channelDepth.red : 8
channelDepth.green : 8
channelDepth.blue : 8
pixels : 3107924
renderingIntent : Perceptual
gamma : 0.454545
backgroundColor : #FFFFFFFF
borderColor : #DFDFDFFF
matteColor : #BDBDBDFF
transparentColor : #00000000
interlace : None
intensity : Undefined
compose : Over
pageGeometry.width : 1522
pageGeometry.height : 2042
pageGeometry.x : 0
pageGeometry.y : 0
dispose : Undefined
iterations : 0
compression : Zip
orientation : Undefined
properties.png:IHDR.bit-depth-orig : 8
properties.png:IHDR.bit_depth : 8
properties.png:IHDR.color-type-orig : 6
properties.png:IHDR.color_type : 6 (RGBA)
properties.png:IHDR.interlace_method : 0 (Not interlaced)
properties.png:IHDR.width,height : 1522, 2042
properties.png:sRGB : intent=0 (Perceptual Intent)
properties.signature : da716ceb3c7b6a31b7723e5ee2894d8eca58a9d18301ce2012174960169ba0f3
tainted :
filesize : 213314
numberPixels : 3.10792M
filename : f4d2c71197a14b514b4effdebbdaaddd2bf1b0e8f879e681565189060590f21d.png
name : f4d2c71197a14b514b4effdebbdaaddd2bf1b0e8f879e681565189060590f21d.png
format : PNG
formatDescription : Portable Network Graphics
mimeType : image/png
class : DirectClass
geometry.width : 1522
geometry.height : 2042
geometry.x : 0
geometry.y : 0
units : Undefined
type : TrueColorAlpha
endianess : Undefined
colorspace : sRGB
depth : 8
baseDepth : 8
channelDepth.alpha : 1
channelDepth.red : 8
channelDepth.green : 8
channelDepth.blue : 8
pixels : 3107924
renderingIntent : Perceptual
gamma : 0.454545
backgroundColor : #FFFFFFFF
borderColor : #DFDFDFFF
matteColor : #BDBDBDFF
transparentColor : #00000000
interlace : None
intensity : Undefined
compose : Over
pageGeometry.width : 1522
pageGeometry.height : 2042
pageGeometry.x : 0
pageGeometry.y : 0
dispose : Undefined
iterations : 0
compression : Zip
orientation : Undefined
properties.png:IHDR.bit-depth-orig : 8
properties.png:IHDR.bit_depth : 8
properties.png:IHDR.color-type-orig : 6
properties.png:IHDR.color_type : 6 (RGBA)
properties.png:IHDR.interlace_method : 0 (Not interlaced)
properties.png:IHDR.width,height : 1522, 2042
properties.png:sRGB : intent=0 (Perceptual Intent)
properties.signature : da716ceb3c7b6a31b7723e5ee2894d8eca58a9d18301ce2012174960169ba0f3
tainted :
filesize : 213314
numberPixels : 3.10792M
filename : f4d2c71197a14b514b4effdebbdaaddd2bf1b0e8f879e681565189060590f21d.png
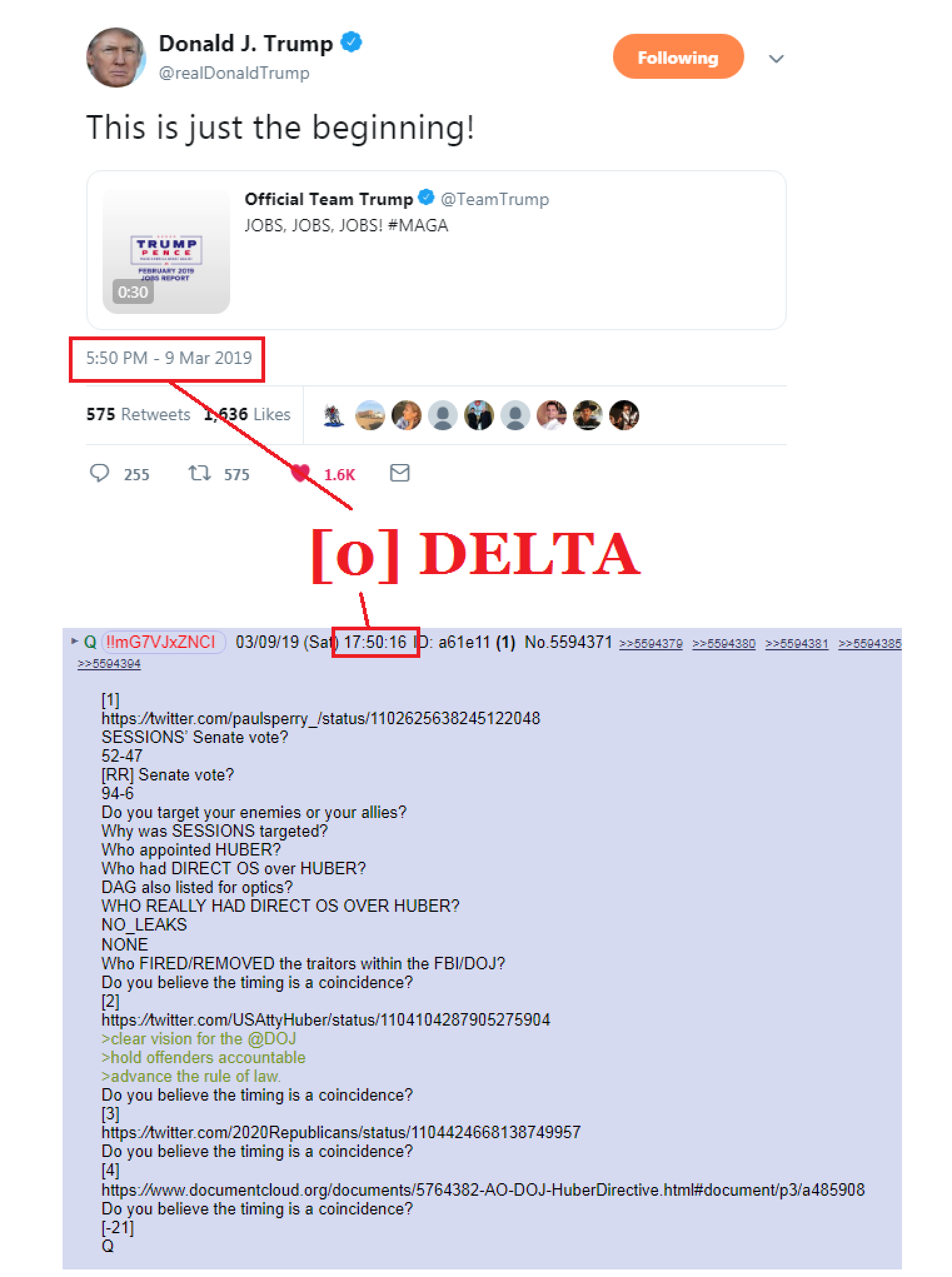
>>5594371
Image Search Tags:
>>5594428
Statistically impossible?
Q
Statistically impossible?
Q
Display Options
Delta to next: 0 D_00:07:12 (seconds total: 432) (9) (9)
Q!!mG7VJxZNCI 03/09/2019 18:17:45 ID: a61e11
8chan/qresearch: 5594916Q Clock [ Min: 37 | :25/:55 Mir: 13 | 180 Mir: 7 | :35/:05 Mir: 33 ]
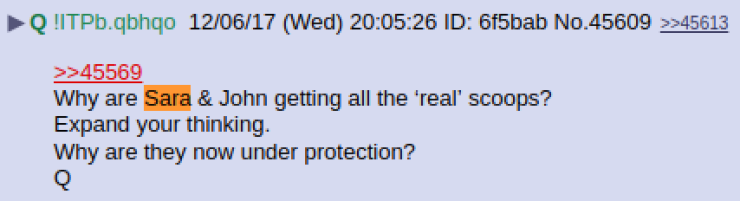
Image Name: Sara-A.-Carter-Q-ITPb.qbhqo-12062017-Wed-200526-6f5bab-No.45609.png
Filename: 4c96b530f377090cf86435e7a1cc3356bde091cec8e31641f8d6728e6bc78b25.png
EXIF DATA
name : 4c96b530f377090cf86435e7a1cc3356bde091cec8e31641f8d6728e6bc78b25.png
format : PNG
formatDescription : Portable Network Graphics
mimeType : image/png
class : DirectClass
geometry.width : 740
geometry.height : 201
geometry.x : 0
geometry.y : 0
units : Undefined
type : TrueColor
endianess : Undefined
colorspace : sRGB
depth : 8
baseDepth : 8
channelDepth.red : 8
channelDepth.green : 8
channelDepth.blue : 8
pixels : 148740
renderingIntent : Perceptual
gamma : 0.454545
backgroundColor : #FFFFFF
borderColor : #DFDFDF
matteColor : #BDBDBD
transparentColor : #000000
interlace : None
intensity : Undefined
compose : Over
pageGeometry.width : 740
pageGeometry.height : 201
pageGeometry.x : 0
pageGeometry.y : 0
dispose : Undefined
iterations : 0
compression : Zip
orientation : Undefined
properties.png:IHDR.bit-depth-orig : 8
properties.png:IHDR.bit_depth : 8
properties.png:IHDR.color-type-orig : 2
properties.png:IHDR.color_type : 2 (Truecolor)
properties.png:IHDR.interlace_method : 0 (Not interlaced)
properties.png:IHDR.width,height : 740, 201
properties.png:sRGB : intent=0 (Perceptual Intent)
properties.png:text : 1 tEXt/zTXt/iTXt chunks were found
properties.signature : 720b0d7acdf4b53c375de20914a130a32396d2ae2f1ff9b2e385c4e6274a9e3a
properties.Software : gnome-screenshot
tainted :
filesize : 55353
numberPixels : 148740
filename : 4c96b530f377090cf86435e7a1cc3356bde091cec8e31641f8d6728e6bc78b25.png
name : 4c96b530f377090cf86435e7a1cc3356bde091cec8e31641f8d6728e6bc78b25.png
format : PNG
formatDescription : Portable Network Graphics
mimeType : image/png
class : DirectClass
geometry.width : 740
geometry.height : 201
geometry.x : 0
geometry.y : 0
units : Undefined
type : TrueColor
endianess : Undefined
colorspace : sRGB
depth : 8
baseDepth : 8
channelDepth.red : 8
channelDepth.green : 8
channelDepth.blue : 8
pixels : 148740
renderingIntent : Perceptual
gamma : 0.454545
backgroundColor : #FFFFFF
borderColor : #DFDFDF
matteColor : #BDBDBD
transparentColor : #000000
interlace : None
intensity : Undefined
compose : Over
pageGeometry.width : 740
pageGeometry.height : 201
pageGeometry.x : 0
pageGeometry.y : 0
dispose : Undefined
iterations : 0
compression : Zip
orientation : Undefined
properties.png:IHDR.bit-depth-orig : 8
properties.png:IHDR.bit_depth : 8
properties.png:IHDR.color-type-orig : 2
properties.png:IHDR.color_type : 2 (Truecolor)
properties.png:IHDR.interlace_method : 0 (Not interlaced)
properties.png:IHDR.width,height : 740, 201
properties.png:sRGB : intent=0 (Perceptual Intent)
properties.png:text : 1 tEXt/zTXt/iTXt chunks were found
properties.signature : 720b0d7acdf4b53c375de20914a130a32396d2ae2f1ff9b2e385c4e6274a9e3a
properties.Software : gnome-screenshot
tainted :
filesize : 55353
numberPixels : 148740
filename : 4c96b530f377090cf86435e7a1cc3356bde091cec8e31641f8d6728e6bc78b25.png
Image Search Tags:
https://twitter.com/SaraCarterDC/status/1104373637036032000
Define 'Protection'.
Q
Define 'Protection'.
Q
Display Options
Delta to next: 0 D_00:04:48 (seconds total: 288) (18) (9)
Q!!mG7VJxZNCI 03/09/2019 18:12:57 ID: a61e11
8chan/qresearch: 5594813Q Clock [ Min: 37 | :25/:55 Mir: 13 | 180 Mir: 7 | :35/:05 Mir: 33 ]
Nellie Ohr > C_A?
There are others within the FBI/DOJ linked to the C_A.
https://www.washingtonpost.com/local/when-ex-spies-go-rogue-by-becoming-lawmakers/2019/01/01/9890c4da-095c-11e9-a3f0-71c95106d96a_story.html?noredirect=on&utm_term=.df98c57998eb
What access does a House member have?
What access does a House Committee member have?
Think [Brennan] spy campaign > US SENATE
What happens when the C_A targets [spy insertion] the Executive, House, Senate, DOJ, FBI, State, etc branches of the UNITED STATES GOV?
How many so-called 'former' C_A agents ran for House elections in 2018?
What party?
[D]
What happens when the C_A targets [spy + tech insertion] of GOOG, FB [LifeLog], Twitter, etc etc?
https://www.foxnews.com/tech/mark-zuckerbergs-conference-room-has-a-secret-panic-chute-report-says
What happens when people wake up to the fact that FB is a cover for LifeLog [DARPA]?
What happens when people discover all RT data [inputs + listening/camera/GPS meta] is being harvested and made accessible to Langley?
Charter of the NSA? DOMESTIC + FOREIGN?
Charter of the C_A? FOREIGN (NOT DOMESTIC (FORBID LAW))
Why is the C_A conducting an active umbrella collection campaign [stringer tangents to 9] against all US citizens through LifeLog [FB] absorb/tan targeting?
Bypass data encryption on phone/tablet etc?
Primary focus on elected officials?
Primary focus on elected officials in key sub committees?
Can activation occur of 'recording' local on device pre SCIF entry?
No logs.
No keys.
Ghost in-Ghost out.
People only engage security (+ escape vehicles) when they have something very serious to FEAR.
What is that FEAR for MZ?
Q
There are others within the FBI/DOJ linked to the C_A.
https://www.washingtonpost.com/local/when-ex-spies-go-rogue-by-becoming-lawmakers/2019/01/01/9890c4da-095c-11e9-a3f0-71c95106d96a_story.html?noredirect=on&utm_term=.df98c57998eb
What access does a House member have?
What access does a House Committee member have?
Think [Brennan] spy campaign > US SENATE
What happens when the C_A targets [spy insertion] the Executive, House, Senate, DOJ, FBI, State, etc branches of the UNITED STATES GOV?
How many so-called 'former' C_A agents ran for House elections in 2018?
What party?
[D]
What happens when the C_A targets [spy + tech insertion] of GOOG, FB [LifeLog], Twitter, etc etc?
https://www.foxnews.com/tech/mark-zuckerbergs-conference-room-has-a-secret-panic-chute-report-says
What happens when people wake up to the fact that FB is a cover for LifeLog [DARPA]?
What happens when people discover all RT data [inputs + listening/camera/GPS meta] is being harvested and made accessible to Langley?
Charter of the NSA? DOMESTIC + FOREIGN?
Charter of the C_A? FOREIGN (NOT DOMESTIC (FORBID LAW))
Why is the C_A conducting an active umbrella collection campaign [stringer tangents to 9] against all US citizens through LifeLog [FB] absorb/tan targeting?
Bypass data encryption on phone/tablet etc?
Primary focus on elected officials?
Primary focus on elected officials in key sub committees?
Can activation occur of 'recording' local on device pre SCIF entry?
No logs.
No keys.
Ghost in-Ghost out.
People only engage security (+ escape vehicles) when they have something very serious to FEAR.
What is that FEAR for MZ?
Q
Display Options
Delta to next: 0 D_00:18:55 (seconds total: 1135) (10) (1)
Q!!mG7VJxZNCI 03/09/2019 17:54:02 ID: a61e11
8chan/qresearch: 5594421Q Clock [ Min: 37 | :25/:55 Mir: 13 | 180 Mir: 7 | :35/:05 Mir: 33 ]
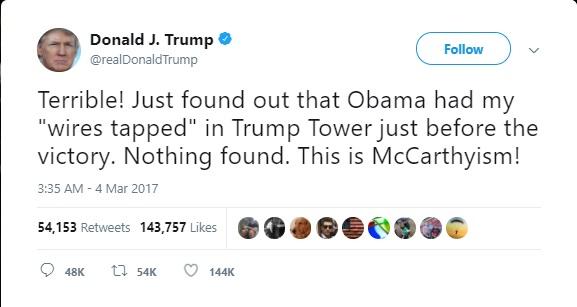
Image Name: w604w86fp3b01.jpg
Filename: fb1a17c26ab6a70d4a87d3d425e2ec9244bf4a21ac3c2e99bee5826d7ef840b1.jpg
EXIF DATA
name : fb1a17c26ab6a70d4a87d3d425e2ec9244bf4a21ac3c2e99bee5826d7ef840b1.jpg
format : JPEG
formatDescription : Joint Photographic Experts Group JFIF format
mimeType : image/jpeg
class : DirectClass
geometry.width : 577
geometry.height : 307
geometry.x : 0
geometry.y : 0
units : Undefined
type : TrueColor
endianess : Undefined
colorspace : sRGB
depth : 8
baseDepth : 8
channelDepth.red : 8
channelDepth.green : 8
channelDepth.blue : 8
pixels : 177139
renderingIntent : Perceptual
gamma : 0.454545
backgroundColor : #FFFFFF
borderColor : #DFDFDF
matteColor : #BDBDBD
transparentColor : #000000
interlace : None
intensity : Undefined
compose : Over
pageGeometry.width : 577
pageGeometry.height : 307
pageGeometry.x : 0
pageGeometry.y : 0
dispose : Undefined
iterations : 0
compression : JPEG
quality : 75
orientation : Undefined
properties.jpeg:colorspace : 2
properties.jpeg:sampling-factor : 2x2,1x1,1x1
properties.signature : bc7cad8e93e29cb1091407dd58851f12342b72141a7df3dfe474945e8713933b
tainted :
filesize : 23268
numberPixels : 177139
filename : fb1a17c26ab6a70d4a87d3d425e2ec9244bf4a21ac3c2e99bee5826d7ef840b1.jpg
name : fb1a17c26ab6a70d4a87d3d425e2ec9244bf4a21ac3c2e99bee5826d7ef840b1.jpg
format : JPEG
formatDescription : Joint Photographic Experts Group JFIF format
mimeType : image/jpeg
class : DirectClass
geometry.width : 577
geometry.height : 307
geometry.x : 0
geometry.y : 0
units : Undefined
type : TrueColor
endianess : Undefined
colorspace : sRGB
depth : 8
baseDepth : 8
channelDepth.red : 8
channelDepth.green : 8
channelDepth.blue : 8
pixels : 177139
renderingIntent : Perceptual
gamma : 0.454545
backgroundColor : #FFFFFF
borderColor : #DFDFDF
matteColor : #BDBDBD
transparentColor : #000000
interlace : None
intensity : Undefined
compose : Over
pageGeometry.width : 577
pageGeometry.height : 307
pageGeometry.x : 0
pageGeometry.y : 0
dispose : Undefined
iterations : 0
compression : JPEG
quality : 75
orientation : Undefined
properties.jpeg:colorspace : 2
properties.jpeg:sampling-factor : 2x2,1x1,1x1
properties.signature : bc7cad8e93e29cb1091407dd58851f12342b72141a7df3dfe474945e8713933b
tainted :
filesize : 23268
numberPixels : 177139
filename : fb1a17c26ab6a70d4a87d3d425e2ec9244bf4a21ac3c2e99bee5826d7ef840b1.jpg
Image Search Tags:
The President of the United States told you who authorized the targeting.
Q
Q
Display Options
Delta to next: 0 D_00:03:46 (seconds total: 226) (10) (1)
Q!!mG7VJxZNCI 03/09/2019 17:50:16 ID: a61e11
8chan/qresearch: 5594371Q Clock [ Min: 37 | :25/:55 Mir: 13 | 180 Mir: 7 | :35/:05 Mir: 33 ]
[1]
https://twitter.com/paulsperry_/status/1102625638245122048
SESSIONS’ Senate vote?
52-47
[RR] Senate vote?
94-6
Do you target your enemies or your allies?
Why was SESSIONS targeted?
Who appointed HUBER?
Who had DIRECT OS over HUBER?
DAG also listed for optics?
WHO REALLY HAD DIRECT OS OVER HUBER?
NO_LEAKS
NONE
Who FIRED/REMOVED the traitors within the FBI/DOJ?
Do you believe the timing is a coincidence?
[2]
https://twitter.com/USAttyHuber/status/1104104287905275904
>clear vision for the @DOJ
>hold offenders accountable
>advance the rule of law.
Do you believe the timing is a coincidence?
[3]
https://twitter.com/2020Republicans/status/1104424668138749957
Do you believe the timing is a coincidence?
[4]
https://www.documentcloud.org/documents/5764382-AO-DOJ-HuberDirective.html#document/p3/a485908
Do you believe the timing is a coincidence?
[-21]
Q
https://twitter.com/paulsperry_/status/1102625638245122048
SESSIONS’ Senate vote?
52-47
[RR] Senate vote?
94-6
Do you target your enemies or your allies?
Why was SESSIONS targeted?
Who appointed HUBER?
Who had DIRECT OS over HUBER?
DAG also listed for optics?
WHO REALLY HAD DIRECT OS OVER HUBER?
NO_LEAKS
NONE
Who FIRED/REMOVED the traitors within the FBI/DOJ?
Do you believe the timing is a coincidence?
[2]
https://twitter.com/USAttyHuber/status/1104104287905275904
>clear vision for the @DOJ
>hold offenders accountable
>advance the rule of law.
Do you believe the timing is a coincidence?
[3]
https://twitter.com/2020Republicans/status/1104424668138749957
Do you believe the timing is a coincidence?
[4]
https://www.documentcloud.org/documents/5764382-AO-DOJ-HuberDirective.html#document/p3/a485908
Do you believe the timing is a coincidence?
[-21]
Q
Display Options
Delta to next: 1 D_18:05:06 (seconds total: 151506) (18) (9)
Q!!mG7VJxZNCI 03/07/2019 23:45:10 ID: d6e0f4
8chan/qresearch: 5569577Q Clock [ Min: 35 | :25/:55 Mir: 15 | 180 Mir: 5 | :35/:05 Mir: 35 ]
http://www.bing.com/news/search?q=facebook&qft=interval%3d%227%22&form=PTFTNR
[Parts 3-9 coming soon]
Q
[Parts 3-9 coming soon]
Q
Display Options
Delta to next: 0 D_00:16:16 (seconds total: 976) (22) (4)
Q!!mG7VJxZNCI 03/07/2019 23:28:54 ID: 285835
8chan/qresearch: 5569206Q Clock [ Min: 35 | :25/:55 Mir: 15 | 180 Mir: 5 | :35/:05 Mir: 35 ]

Image Name: D0_uJzGX4AASbQp.jpg
Filename: 044e8e07d846359be22d1b45d2259a962442b89755be4a61ad0f37eede1367ea.jpg
EXIF DATA
name : 044e8e07d846359be22d1b45d2259a962442b89755be4a61ad0f37eede1367ea.jpg
format : JPEG
formatDescription : Joint Photographic Experts Group JFIF format
mimeType : image/jpeg
class : DirectClass
geometry.width : 640
geometry.height : 786
geometry.x : 0
geometry.y : 0
units : Undefined
type : TrueColor
endianess : Undefined
colorspace : sRGB
depth : 8
baseDepth : 8
channelDepth.red : 8
channelDepth.green : 8
channelDepth.blue : 8
pixels : 503040
renderingIntent : Perceptual
gamma : 0.454545
backgroundColor : #FFFFFF
borderColor : #DFDFDF
matteColor : #BDBDBD
transparentColor : #000000
interlace : JPEG
intensity : Undefined
compose : Over
pageGeometry.width : 640
pageGeometry.height : 786
pageGeometry.x : 0
pageGeometry.y : 0
dispose : Undefined
iterations : 0
compression : JPEG
quality : 85
orientation : Undefined
properties.jpeg:colorspace : 2
properties.jpeg:sampling-factor : 2x2,1x1,1x1
properties.signature : 1e913457310dded911fe43ad6d39fa262809d37399c3d99e1f6f03a8ac63c87a
tainted :
filesize : 67386
numberPixels : 503040
filename : 044e8e07d846359be22d1b45d2259a962442b89755be4a61ad0f37eede1367ea.jpg
name : 044e8e07d846359be22d1b45d2259a962442b89755be4a61ad0f37eede1367ea.jpg
format : JPEG
formatDescription : Joint Photographic Experts Group JFIF format
mimeType : image/jpeg
class : DirectClass
geometry.width : 640
geometry.height : 786
geometry.x : 0
geometry.y : 0
units : Undefined
type : TrueColor
endianess : Undefined
colorspace : sRGB
depth : 8
baseDepth : 8
channelDepth.red : 8
channelDepth.green : 8
channelDepth.blue : 8
pixels : 503040
renderingIntent : Perceptual
gamma : 0.454545
backgroundColor : #FFFFFF
borderColor : #DFDFDF
matteColor : #BDBDBD
transparentColor : #000000
interlace : JPEG
intensity : Undefined
compose : Over
pageGeometry.width : 640
pageGeometry.height : 786
pageGeometry.x : 0
pageGeometry.y : 0
dispose : Undefined
iterations : 0
compression : JPEG
quality : 85
orientation : Undefined
properties.jpeg:colorspace : 2
properties.jpeg:sampling-factor : 2x2,1x1,1x1
properties.signature : 1e913457310dded911fe43ad6d39fa262809d37399c3d99e1f6f03a8ac63c87a
tainted :
filesize : 67386
numberPixels : 503040
filename : 044e8e07d846359be22d1b45d2259a962442b89755be4a61ad0f37eede1367ea.jpg
Image Search Tags:
We stand TOGETHER in this FIGHT.
WWG1WGA!!!
Q
WWG1WGA!!!
Q
Display Options
Delta to next: 0 D_00:07:14 (seconds total: 434) (11) (2)
Q!!mG7VJxZNCI 03/07/2019 23:21:40 ID: 285835
8chan/qresearch: 5569036Q Clock [ Min: 35 | :25/:55 Mir: 15 | 180 Mir: 5 | :35/:05 Mir: 35 ]
Image Name: DrYsi4PXcAAsIc0.jpg
Filename: 55fb379e013810802b3624a6e232df45ba6e2ef71c8ce8cd5af9b6a210d74022.jpg
EXIF DATA
name : 55fb379e013810802b3624a6e232df45ba6e2ef71c8ce8cd5af9b6a210d74022.jpg
format : JPEG
formatDescription : Joint Photographic Experts Group JFIF format
mimeType : image/jpeg
class : DirectClass
geometry.width : 997
geometry.height : 1200
geometry.x : 0
geometry.y : 0
units : Undefined
type : TrueColor
endianess : Undefined
colorspace : sRGB
depth : 8
baseDepth : 8
channelDepth.red : 8
channelDepth.green : 8
channelDepth.blue : 8
pixels : 1196400
renderingIntent : Perceptual
gamma : 0.454545
backgroundColor : #FFFFFF
borderColor : #DFDFDF
matteColor : #BDBDBD
transparentColor : #000000
interlace : JPEG
intensity : Undefined
compose : Over
pageGeometry.width : 997
pageGeometry.height : 1200
pageGeometry.x : 0
pageGeometry.y : 0
dispose : Undefined
iterations : 0
compression : JPEG
quality : 85
orientation : Undefined
properties.icc:copyright : Google Inc. 2016
properties.icc:description : Google Skia
properties.jpeg:colorspace : 2
properties.jpeg:sampling-factor : 2x2,1x1,1x1
properties.signature : a34edfacdd72c639c13a5b46c7c983f155844284e348d53928839575dd2fcf8b
profiles.icc :
tainted :
filesize : 169248
numberPixels : 1196400
filename : 55fb379e013810802b3624a6e232df45ba6e2ef71c8ce8cd5af9b6a210d74022.jpg
name : 55fb379e013810802b3624a6e232df45ba6e2ef71c8ce8cd5af9b6a210d74022.jpg
format : JPEG
formatDescription : Joint Photographic Experts Group JFIF format
mimeType : image/jpeg
class : DirectClass
geometry.width : 997
geometry.height : 1200
geometry.x : 0
geometry.y : 0
units : Undefined
type : TrueColor
endianess : Undefined
colorspace : sRGB
depth : 8
baseDepth : 8
channelDepth.red : 8
channelDepth.green : 8
channelDepth.blue : 8
pixels : 1196400
renderingIntent : Perceptual
gamma : 0.454545
backgroundColor : #FFFFFF
borderColor : #DFDFDF
matteColor : #BDBDBD
transparentColor : #000000
interlace : JPEG
intensity : Undefined
compose : Over
pageGeometry.width : 997
pageGeometry.height : 1200
pageGeometry.x : 0
pageGeometry.y : 0
dispose : Undefined
iterations : 0
compression : JPEG
quality : 85
orientation : Undefined
properties.icc:copyright : Google Inc. 2016
properties.icc:description : Google Skia
properties.jpeg:colorspace : 2
properties.jpeg:sampling-factor : 2x2,1x1,1x1
properties.signature : a34edfacdd72c639c13a5b46c7c983f155844284e348d53928839575dd2fcf8b
profiles.icc :
tainted :
filesize : 169248
numberPixels : 1196400
filename : 55fb379e013810802b3624a6e232df45ba6e2ef71c8ce8cd5af9b6a210d74022.jpg
Image Search Tags:
Display Options
Delta to next: 0 D_00:07:21 (seconds total: 441) (9) (9)
Q!!mG7VJxZNCI 03/07/2019 23:14:19 ID: 285835
8chan/qresearch: 5568867Q Clock [ Min: 35 | :25/:55 Mir: 15 | 180 Mir: 5 | :35/:05 Mir: 35 ]
https://twitter.com/Davidwmiller91/status/1103826672762146817
Keep the calendar up-to-date, Patriot.
Check off and log.
Future proves past.
Q
Keep the calendar up-to-date, Patriot.
Check off and log.
Future proves past.
Q
Display Options
Delta to next: 0 D_00:06:26 (seconds total: 386) (17) (8)
Q!!mG7VJxZNCI 03/07/2019 23:07:53 ID: f9e971
8chan/qresearch: 5568772Q Clock [ Min: 35 | :25/:55 Mir: 15 | 180 Mir: 5 | :35/:05 Mir: 35 ]
https://twitter.com/SenBlumenthal/status/1103710332994887682
Glimpse of something much bigger to come?
Actions have consequences.
Remember, it goes both ways.
Nobody is safe.
Leak was plugged.
Q
Glimpse of something much bigger to come?
Actions have consequences.
Remember, it goes both ways.
Nobody is safe.
Leak was plugged.
Q
Display Options
Delta to next: 0 D_00:07:55 (seconds total: 475) (16) (7)
Q!!mG7VJxZNCI 03/07/2019 22:59:58 ID: f9e971
8chan/qresearch: 5568629Q Clock [ Min: 35 | :25/:55 Mir: 15 | 180 Mir: 5 | :35/:05 Mir: 35 ]
Delta to Reply: 0 D_03:28:50 (seconds total: 12530) (11) (2)
Epoch: 1552005068 (32) (5)
Anonymous 03/07/2019 19:31:08 ID:9a6a8f 8chan/qresearch: 5565314
Keking out right now. Pretty sure I found something. Rip me apart if I’m wrong though. So many shills on here. You’re missing crumbs. Look here, not [here]. Responding to post 2996 Q says, “how is that possible for a ‘supposed’ non_gov entity?”
How is it possible that FB tracks data even when the app is deleted? In post 2993 (3/7/109) Q is calling out @Snowden. So I used the filter to find posts relating to WikiLeaks. Q’s post from July 31, 2018 is a screenshot of the Wikileaks Vault 7… released MARCH 7. Sounds confusing just trying to show you my thought process, stay with me, it makes sense.
“Unlike bullets, bombs or missiles, most CIA malware is designed to live for days or even years after it has reached its 'target'. CIA malware does not "explode on impact" but rather permanently infests its target. In order to infect target's device, copies of the malware must be placed on the target's devices, giving physical possession of the malware to the target. To exfiltrate data back to the CIA or to await further instructions the malware must communicate with CIA Command & Control (C2) systems placed on internet connected servers. But such servers are typically not approved to hold classified information, so CIA command and control systems are also made unclassified.” FROM VAULT 7
Links below that direct you to user forums on how to not leave a digital fingerprint that can be associated with the CIA, and how to construct an imitation fingerprint. Using Facebook as their ‘fingerprint’ they are able to install malware on peoples’ phones, tablets, and computers which relay all data back to a central server using HIVE.
I suggest all anons who have given up life to research this shit like me should read this document to completion.
I noticed the enormous amount of comparisons between “packets of data” and “bombs”, dunno why probably just autistic. I looked back in the Qmap and on March 5, 2019 an anon posted how London Police “called them bombs not suspicious packages” Q responds in 2974 with “Fire”.
I went into Vault 7 Projects, search for “fire”….
“Angelfire is an implant comprised of five components: Solartime, Wolfcreek, Keystone (previously MagicWand), BadMFS, and the Windows Transitory File system”
FUCKING KEYSTONE KEK
“Keystone is part of the Wolfcreek implant and responsible for starting malicious user applications. Loaded implants never touch the file system, so there is very little forensic evidence that the process was ever ran.” This makes post Q 381 much easier to understand
“We Won’t telegraph our moves to the ENEMY.
We will however light a FIRE to flush them out.”
Q
Q is saying that they are using the Anglefire to predict the Deep State’s moves without being detected. In the user files it says a key must be used to open magicwand (keystone). In Q post 270 he says that ADM R/NSA (W&W) + POTUS/USMIL = Apply the Keystone. Paint the Picture. In post 167 Q says POTUS opened the door of all doors. Expand your thinking. What is the keystone? Now this could be confirmation bias but based off of what we just read we can now infer that Q was saying trump gave Admiral Rogers permission to use Keystone and Activate malware in order to collect data on DS. Furthermore who uses a magicwand? A wizard. (W&W)
How is it possible that FB tracks data even when the app is deleted? In post 2993 (3/7/109) Q is calling out @Snowden. So I used the filter to find posts relating to WikiLeaks. Q’s post from July 31, 2018 is a screenshot of the Wikileaks Vault 7… released MARCH 7. Sounds confusing just trying to show you my thought process, stay with me, it makes sense.
“Unlike bullets, bombs or missiles, most CIA malware is designed to live for days or even years after it has reached its 'target'. CIA malware does not "explode on impact" but rather permanently infests its target. In order to infect target's device, copies of the malware must be placed on the target's devices, giving physical possession of the malware to the target. To exfiltrate data back to the CIA or to await further instructions the malware must communicate with CIA Command & Control (C2) systems placed on internet connected servers. But such servers are typically not approved to hold classified information, so CIA command and control systems are also made unclassified.” FROM VAULT 7
Links below that direct you to user forums on how to not leave a digital fingerprint that can be associated with the CIA, and how to construct an imitation fingerprint. Using Facebook as their ‘fingerprint’ they are able to install malware on peoples’ phones, tablets, and computers which relay all data back to a central server using HIVE.
I suggest all anons who have given up life to research this shit like me should read this document to completion.
I noticed the enormous amount of comparisons between “packets of data” and “bombs”, dunno why probably just autistic. I looked back in the Qmap and on March 5, 2019 an anon posted how London Police “called them bombs not suspicious packages” Q responds in 2974 with “Fire”.
I went into Vault 7 Projects, search for “fire”….
“Angelfire is an implant comprised of five components: Solartime, Wolfcreek, Keystone (previously MagicWand), BadMFS, and the Windows Transitory File system”
FUCKING KEYSTONE KEK
“Keystone is part of the Wolfcreek implant and responsible for starting malicious user applications. Loaded implants never touch the file system, so there is very little forensic evidence that the process was ever ran.” This makes post Q 381 much easier to understand
“We Won’t telegraph our moves to the ENEMY.
We will however light a FIRE to flush them out.”
Q
Q is saying that they are using the Anglefire to predict the Deep State’s moves without being detected. In the user files it says a key must be used to open magicwand (keystone). In Q post 270 he says that ADM R/NSA (W&W) + POTUS/USMIL = Apply the Keystone. Paint the Picture. In post 167 Q says POTUS opened the door of all doors. Expand your thinking. What is the keystone? Now this could be confirmation bias but based off of what we just read we can now infer that Q was saying trump gave Admiral Rogers permission to use Keystone and Activate malware in order to collect data on DS. Furthermore who uses a magicwand? A wizard. (W&W)
>>5565314 (/pb)
Something you should explore further.
Impressive, most impressive.
Q
Something you should explore further.
Impressive, most impressive.
Q
Display Options
Delta to next: 0 D_20:27:28 (seconds total: 73648) (28) (1)
Q!!mG7VJxZNCI 03/07/2019 02:32:30 ID: 9950b1
8chan/qresearch: 5553520Q Clock [ Min: 35 | :25/:55 Mir: 15 | 180 Mir: 5 | :35/:05 Mir: 35 ]
Display Options
Delta to next: 0 D_00:25:25 (seconds total: 1525) (13) (4)
Q!!mG7VJxZNCI 03/07/2019 02:07:05 ID: 1e3478
8chan/qresearch: 5553154Q Clock [ Min: 35 | :25/:55 Mir: 15 | 180 Mir: 5 | :35/:05 Mir: 35 ]
Delta to Reply: 0 D_00:22:50 (seconds total: 1370) (11) (2)
Epoch: 1551941055 (36) (9)
Anonymous 03/07/2019 01:44:15 ID:54f4cb 8chan/qresearch: 5552800
>>5552746
kek, Q.
MZ gets called out and immeadiately panics.
Really nothing to see here… /s
kek, Q.
MZ gets called out and immeadiately panics.
Really nothing to see here… /s
>>5552800
Other articles prior to posts.
Privacy push to cover for past/future 'exposure' issue re: data release non_marketing.
There is no privacy.
There is no way to turn off (even through app deletion) their ability to extract info.
How is that possible for a 'supposed' non_gov entity?
Phone co's involved?
Phone_wipe resolve?
Q
Other articles prior to posts.
Privacy push to cover for past/future 'exposure' issue re: data release non_marketing.
There is no privacy.
There is no way to turn off (even through app deletion) their ability to extract info.
How is that possible for a 'supposed' non_gov entity?
Phone co's involved?
Phone_wipe resolve?
Q